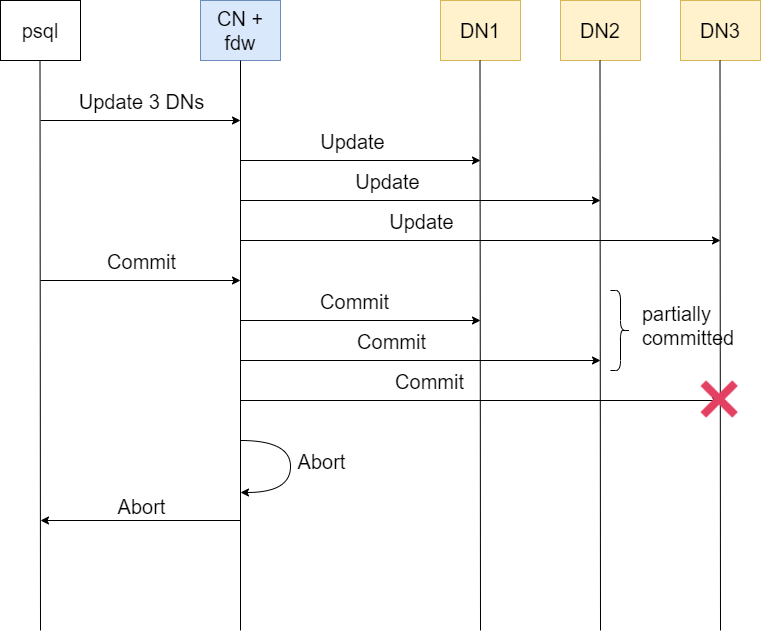
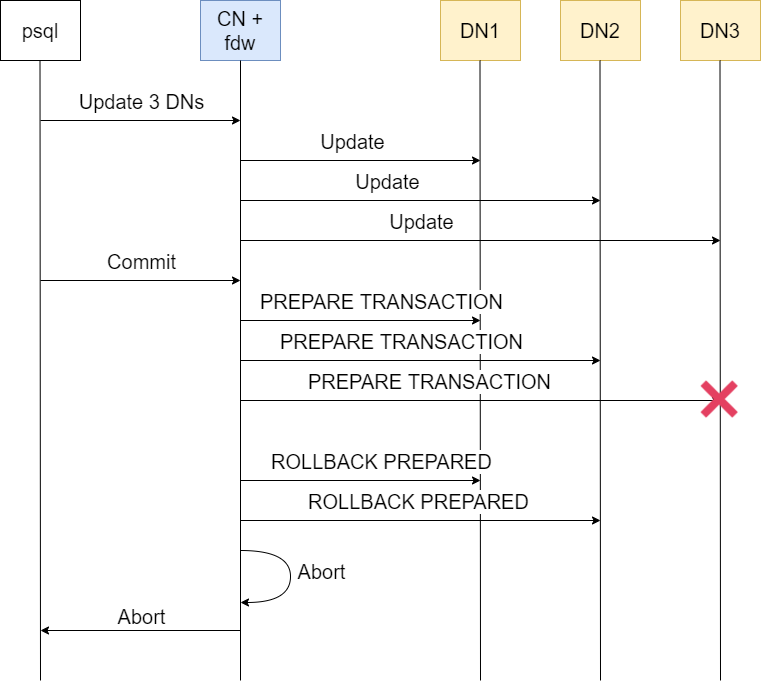
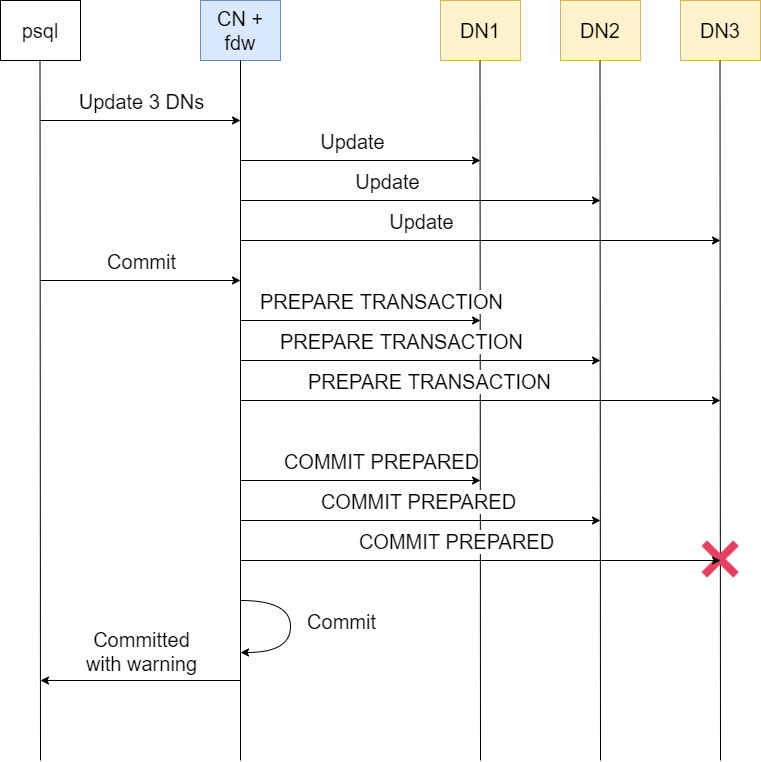
Introduction
Network File System (NFS) is a distributed file system protocol that allows a user on a client node to access files residing on a server node over network much like local storage is accessed. Today in this blog, I will share how to set up both NFSv4 server and client on CentOS7 and run PG on it.
NFS Server
First, install the NFS server components by
yum install nfs-utils |
This will install nfs process on the server machine in which we can go ahead to enable and start the NFS server
systemctl enable nfs |
Create a directory that will be mounted by NFS clients
mkdir /home/myserveruser/sharedir |
In /etc/exports, add a new record like below
/home/myuser/sharedir X.X.X.X(rw,sync,no_subtree_check,no_root_squash) |
This line is allowing a client having IP address of X.X.X.X to mount the directory at /home/myserveruser/sharedir and can do read and write as specified by rw option. For all possible options, refer to the blog here for definition of each options used. This directory will be used to initialized PostgreSQL database cluster by a NFS client over the network.
If more than one client/host will mount the same directory, you will need to include them in /etc/exports as well.
/home/myuser/sharedir X.X.X.X(rw,sync,no_subtree_check,no_root_squash) |
Then, we are ready to restart the NFS service to take account the new changes in /etc/exports
systemctl restart nfs |
Record the userid and groupid of the user associated with the directory to be exported to client. For example, userid = 1009, groupid = 1009
id myuser |
You may also want to ensure that the firewall on centos7 is either disabled or set to allow the NFS traffic to passthrough. You can check the firewall status and add new port to be allowed with the following commands:
sudo firewall-cmd --zone=public --list-all |
NFS Client
First, install the NFS client components by
yum install nfs-utils |
Create a directory on the client side that will be used as the mount point to the NFS server
mkdir /home/myserveruser/sharedir |
Since PostgreSQL cannot be run as root user, we need a way to mount the remote NFS without root privileges. To do that, we need to add one more entry in /etc/fstab
Y.Y.Y.Y:/home/myserveruser/sharedir /home/myclientuser/mountpoint nfs rw,noauto,user 0 0 |
where Y.Y.Y.Y is the IP address of the NFS server that client will connect to, nfs is the type of file system we will mount as, rw means read and write, noauto means the mount point will not be mounted automatically at system startup and user means this mount point can be mounted by a non-root user.
With this new line added to /etc/fstab, you could try mounting it using mount -a command or simply do a reboot
Now, we need to match the userid and groupid of myserveruser on the NFS server side and myclientuser on the NFS side. The user names do not have to be equal, but the userid and groupid must be equal to have the correct permission to access the mounted directory,
To set the userid and groupid of the myclientuser:
usermod -u 1009 myclientuser |
where 1009 is recorded on the NFS server side by the id command.
Please note that the above commands will change the property of the specified user and that will also cause the tool to iteratively change all the files under /home/myclientuser to be the same property given that it is owned by the specified user. This process may take a long time to complete. if you have a huge amount of data there, I would recommend creating a new user instead of changing the userid and groupid. Please note that files outside of specified user’s /home directory will not be changed the properly, which means current user can no longer access them once userid and groupid have been changed.
With all the setup in place, we are now ready to mount NFS:
$ mount /home/clientuser/mountpoint; |
and the folder mountpoint on NFS client side will now reflect to sharedir folder on the NFS server
Finally, we can initialize a new database cluster on the mountpoint on the NFS client side
$ initdb -D /home/clientuser/mountpoint |
and the initial database files should be physically stored on the NFS server side instead of NFS client. This may take longer than usual because the file I/Os are now done over the network via NFS.